


Ransomware is a type of malicious software (malware) that can lock your computer screen and prevent you from accessing your files by encrypting them. Normally, the hacker who sent the ransomware will demand that you pay a fee (ransom) to regain access to your PC and files.
In a typical ransomware incident, you will receive an email containing a legitimate‑looking file attachment or link to a URL. Opening the file or clicking the link will enable malware to automatically install itself onto your computer. The malware then searches for, and encrypts, your files and folders on local, network, and attached drives, and also puts your other networked devices at risk.
Once the hacker has locked or encrypted your files, you may receive a message that looks similar to the following image:
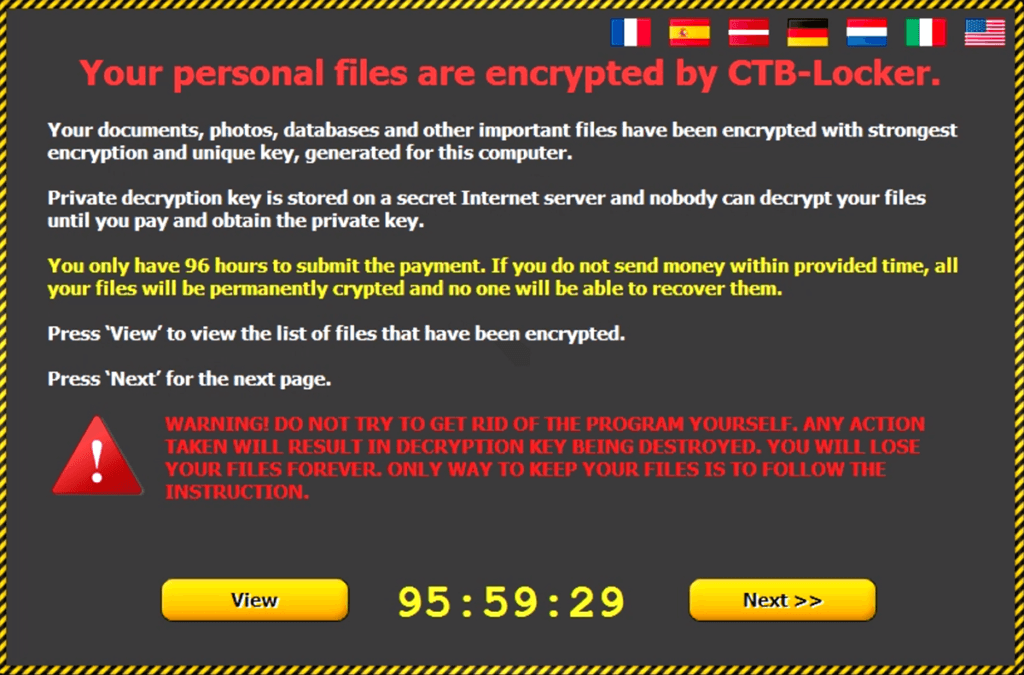
Immediately remove the network cable from your computer and shut down your machine. The quickest way to shut down your computer is to hold down the power button.
Submit an emergency IT support request at the ITS Service Desk.
Malware authors will often try to trick you into downloading malicious files. They disguise their files as email attachments with messages notifying you of a delivery receipt, tax refund, or ticket invoice. The messages might ask you to open the attachment to get the items delivered or receive the money. If you do open the attachments, however, you will end up installing malware on your PC.
Sometimes malicious emails will be easy to spot: they could contain poor spelling and grammar or come from email addresses you have never seen before. These emails, however, also can look like they come from a legitimate business or someone you know. Be careful—some malware can hack your email accounts and send malicious messages to all of your contacts.
If a message creates a strong sense of urgency, is confusing, or seems too good to be true, it could be an attack. Be suspicious—common sense is often your best defense.
Ransomware can download automatically if you click on a malicious website or a website that has been hacked. Be aware—just browsing a corrupted website is enough to transfer malicious code to your computer.
RRC Polytech campuses are located on the lands of Anishinaabe, Ininiwak, Anishininew, Dakota, and Dené, and the National Homeland of the Red River Métis.
We recognize and honour Treaty 3 Territory Shoal Lake 40 First Nation, the source of Winnipeg’s clean drinking water. In addition, we acknowledge Treaty Territories which provide us with access to electricity we use in both our personal and professional lives.